Spies Online Quick Finder
Online Hash Crack is an online service that attempts to recover your lost passwords: - Hashes (e.g. MD5, NTLM, Wordpress.) - Wifi WPA handshakes - Office encrypted files (Word, Excel.) - Apple iTunes Backup - ZIP / RAR / 7-zip Archive - PDF documents. How CrackStation Works CrackStation uses massive pre-computed lookup tables to crack password hashes. These tables store a mapping between the hash of a password, and the correct password for that hash. The hash values are indexed so that it is possible to quickly search the database for a given hash. 279245: e665816: 2020-02-19: IPB/MYBB - md5(md5($salt).md5($pass)) 500: 259: 241. Quick and safe cloud service for opening password protected RAR files. We can recover passwords for all versions of encrypted WinRAR archives. For a free password recovery, upload your file and follow the instructions.
|
|
Cracking Unix Passwords
Translated by ToKsURi
Introduction-
To gain access into a Unix system, its necessary to have a username anda password, and what better place to find them than from /etc/passwd:-) This is the file which holds the list of usernames and passwords inUnix, aswell as other kind of information in relation which each username..The problem is that these passwords are encrypted. Let see the appearenceof one of these files: root:XY53yyh3gMvvE:0:3::/root:/bin/sh
daemon:*:1:5::/:/bin/sh
bin:*:2:2::/bin:/bin/sh
adm:*:4:4::/usr/adm:/bin/sh
uucp:*:5:3::/usr/spool/ucppublic:/usr/lib/uucp/uucico
lp:*:9:7::/usr/spool/lp:/bin/sh
hpdb:*:27:1:ALLBASE:/:/bin/sh
user1:g.um3CCF4uVIk:247:25:DArcy
Martín:/disc/users/pepito:/bin/csh
user2:RckFa8/idTCFg:248:24:Billy Corgan:/disc/users/fulanito:/bin/csh
user3:axX/MxQZr37tA:0:3:James Iha:/disc/users/menganito:/bin/csh
As you can see, each line corresponds to a user, and contains ( in order) the username, the encrypted password, the user_id, the group_id, thereal name, the home directory and the shell loaded at the startup.. Theformat may change slightly, but basically it is this one. As youcan see, each field is separated from the previous and next field by acolom ' : ' In some lines, the password field is ' * ' Thisencrypted password is invalid, that is, they dont belong to an existingpassword, therefore you may not access those accounts. Another detailwe must take into consideration are all those users whose user_id is '0',as ROOT. These users are ROOT by all means, therefore, they havethe same rights as the actual ROOT. As you can observe, 'user3' hasa user_id=0, which means it is a ROOT. In a similar way, the userswithout user_id=0 may still have access to some ROOT actions by thefact that they belong to the ROOT group.

Ok, now we have to 'dencrypt' the passwords. The problem is thatUnix uses a one-way encryption mechanism, which means it cant be 'dencrypted'. Then.. how does the LOGIN checks whether the password is correct? Whathappens is that the system encrypts the password that we enter and it iscompared with the text string belonging to the actual password in the passwdfile. If they are identical then the password is correct and thesystem lets you in. The way of attacking a unix passwd file is preciselythe same as LOGIN does. What the cracker does is encrypt maaaaaaaaaaaaanywords and check if any of the encrypted words match with the encryptedpassword in the passwd file. If they match, we have our password!And if not, we will try on with a different word. For doing thiswe need three things: 1- A word list to encrypt and check. 2- A Listwith the encrypted passwords (passwd file) 3- A program which does allthe job.
STEP ONE: Obtaining the Word List
Be creative. You may write your own word list with names, surnames,famous people, numbers, months, bad words, companies, server namesand the so used sex, love and god. Anything is valid as long as youthink it may be used as a password in the system you want to hack. Luckly, you may find in internet word lists waiting to be checked. One of the most interesting places for obtaining word lists is: ftp://sable.ox.ac.uk/pub/wordlists/. There are many wordlists, but it is slightly slow. Fortunately, thereis a mirror of this server in Spain, at ftp://sun.rediris.es/mirror/sable/wordlists/which goes much more quicker, specially if your internet connection isinside the spanish network. Anyway, youy may always search in Yahooor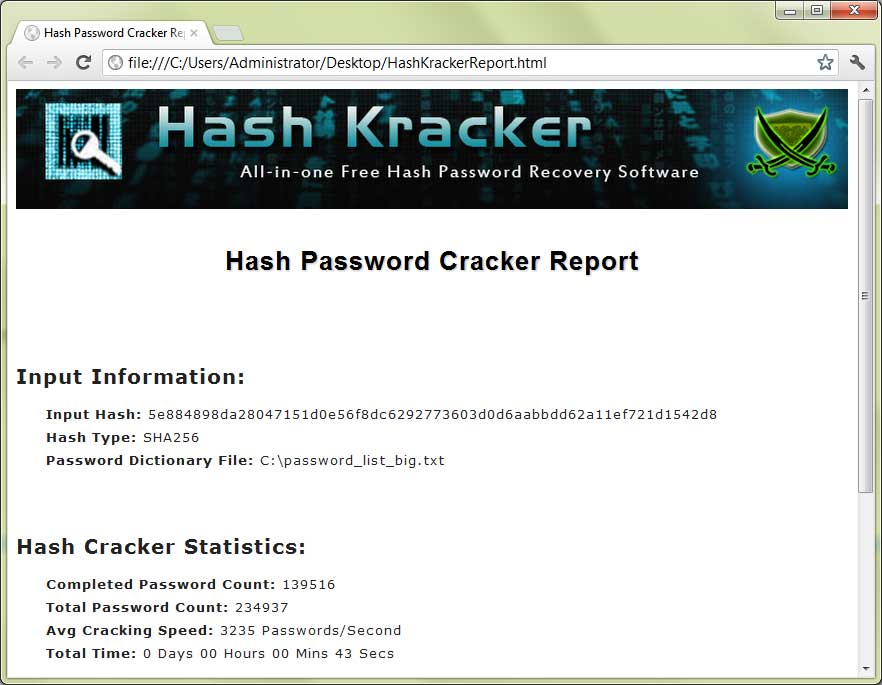
How To Reset Unix Password
wordlis' and you'll find many sites with wordlists. A good tip is to try with the names and surnames of the users of the systemyou are trying to crack.. There is maaaaaaany people who uses as passwordtheir own names or their girlfriend's name. So a word list with thenames and surnames of the users is a good chance of obtaining passwords. Another word which is a common a password is the username itself. Also many people uses 'password'. It is a good recommendation toextract all of the words inside the passwd file and try them as password. For doing this there are many utilities, some of them are even distributedtogether with the cracker. I dont think you'll find very difficultto find a program which extracts the names, surnames and usernames of theusers in a /etc/passwd file. There are even utilities which theironly function is to make word lists.STEP 2: Obtaining the password list
This is slightly more difficult. If you have an account in thesystem you want to hack, you may always do a 'cat /etc/passwd' Ifthey dont have Shadow Passwords or NIS, a list like the one you have seenat the beginning will appear. Else, you will see somehing like this:
root:XY53yyh3gMvvE:0:3::/root:/bin/sh
daemon:*:1:5::/:/bin/sh
bin:*:2:2::/bin:/bin/sh
adm:*:4:4::/usr/adm:/bin/sh
uucp:*:5:3::/usr/spool/ucppublic:/usr/lib/uucp/uucico
lp:*:9:7::/usr/spool/lp:/bin/sh
hpdb:*:27:1:ALLBASE:/:/bin/sh
user1:g.um3CCF4uVIk:247:25:DArcy
Martín:/disc/users/pepito:/bin/csh
user2:RckFa8/idTCFg:248:24:Billy Corgan:/disc/users/fulanito:/bin/csh
user3:axX/MxQZr37tA:0:3:James Iha:/disc/users/menganito:/bin/csh
Unix Change Password Command
where the password will be something like '*' or 'x' or anything whichcontains an asterisc '*' as '*NOPASSWORD*'. In this case, the file/etc/passwd is of no use, as Shadow Passwords or NIS is installed. Then, you may try doing a 'ypcat /etc/passwd' With this you may probablyfind via screen the real list of passwords. In the event you donthave enough rights to run 'ypcat', or if it isnt installed or if afterdoing it junk appears again, you will have to make use of other programsto obtain the passwords. I reccommend you PWGET. It is veryeasy to find, just look for PWGET.TAR.GZ or PWGET.TGZ in any archie, orin Lycos or in Yahoo. Sure you will find it. Once youhave it, you just need to upload it to the server you want to hack, unzipit ('gzip -d -f PWGET.TGZ'), untar it ('tar -x -f PWGET.TAR'), compileit ('cc -o pwget pwget.c') and run it ('./pwget') by which you will seein the screen the password list. If you want the list in a file,you just have to redirect the screen output into a file:$ ./pwget > fileThe same way you will redirect the output under DOS.. Now, for downloadingthe file you may use FTP, Kermit or the ZModem/Ymodem/Xmodem. Fordownloading the file via kermit or Zmodem you will need that your telnetprogram supports this protocols (as NetTerm), and that the Unix machinealso does (that is, it has the neccesary file installed). Kermitis usually installed in all systems:$ kermit
or else
$ ypcat /etc/passwd > file
or else
$ cat /etc/passwd > file
kermit> set file type ascii (or '
Default Unix Password
text', depends onsystems)kermit> set send pack 1000
kermit> set rec pack 1000
kermit> set file type 2 (or 3, as you prefer)
kermit> send fichero
.. Download->Kermit
CTRL+C
kermit> quit
$

.. Download->ZModem
$
Step 3: Cracking the password list
Now that you have the password list and several word lists, you need aprogram which encrypts the words and afterwards checks them with the encryptedpasswords in the password list. There are many programs you may use. Now I will briefly comment the characteristics of the programs (an theirnames, so that you may look for them in the net), but first I would liketo give some tips for obtaining the passwords in less time.Delete from the password file all lines whose password is invalid ('*','*NOPASSWORD*', etc) Arrange the lines of the password file by the two first characters of theencrypted password. Some of the programs I comment, do this automatically,but some dont. With these two steps you may save a lot of time dependingin the cracker you use. Those users who have the password field empty
(user1::101:1:Manolito:/usr/user1:/bin/sh) dont have a passwordat all, therefore they are lines you may delete from the file. Whenyou login, simply by typing the username you will have access. Andin the event it asks you for a password, press ENTER without writing apassword. :-)

Ok, now we have to 'dencrypt' the passwords. The problem is thatUnix uses a one-way encryption mechanism, which means it cant be 'dencrypted'. Then.. how does the LOGIN checks whether the password is correct? Whathappens is that the system encrypts the password that we enter and it iscompared with the text string belonging to the actual password in the passwdfile. If they are identical then the password is correct and thesystem lets you in. The way of attacking a unix passwd file is preciselythe same as LOGIN does. What the cracker does is encrypt maaaaaaaaaaaaanywords and check if any of the encrypted words match with the encryptedpassword in the passwd file. If they match, we have our password!And if not, we will try on with a different word. For doing thiswe need three things: 1- A word list to encrypt and check. 2- A Listwith the encrypted passwords (passwd file) 3- A program which does allthe job.
STEP ONE: Obtaining the Word List
Be creative. You may write your own word list with names, surnames,famous people, numbers, months, bad words, companies, server namesand the so used sex, love and god. Anything is valid as long as youthink it may be used as a password in the system you want to hack. Luckly, you may find in internet word lists waiting to be checked. One of the most interesting places for obtaining word lists is: ftp://sable.ox.ac.uk/pub/wordlists/. There are many wordlists, but it is slightly slow. Fortunately, thereis a mirror of this server in Spain, at ftp://sun.rediris.es/mirror/sable/wordlists/which goes much more quicker, specially if your internet connection isinside the spanish network. Anyway, youy may always search in Yahooor Lycos for 'dictionar'or by 'How To Reset Unix Password
wordlis' and you'll find many sites with wordlists. A good tip is to try with the names and surnames of the users of the systemyou are trying to crack.. There is maaaaaaany people who uses as passwordtheir own names or their girlfriend's name. So a word list with thenames and surnames of the users is a good chance of obtaining passwords. Another word which is a common a password is the username itself. Also many people uses 'password'. It is a good recommendation toextract all of the words inside the passwd file and try them as password. For doing this there are many utilities, some of them are even distributedtogether with the cracker. I dont think you'll find very difficultto find a program which extracts the names, surnames and usernames of theusers in a /etc/passwd file. There are even utilities which theironly function is to make word lists.STEP 2: Obtaining the password list
This is slightly more difficult. If you have an account in thesystem you want to hack, you may always do a 'cat /etc/passwd' Ifthey dont have Shadow Passwords or NIS, a list like the one you have seenat the beginning will appear. Else, you will see somehing like this:
root:XY53yyh3gMvvE:0:3::/root:/bin/sh
daemon:*:1:5::/:/bin/sh
bin:*:2:2::/bin:/bin/sh
adm:*:4:4::/usr/adm:/bin/sh
uucp:*:5:3::/usr/spool/ucppublic:/usr/lib/uucp/uucico
lp:*:9:7::/usr/spool/lp:/bin/sh
hpdb:*:27:1:ALLBASE:/:/bin/sh
user1:g.um3CCF4uVIk:247:25:DArcy
Martín:/disc/users/pepito:/bin/csh
user2:RckFa8/idTCFg:248:24:Billy Corgan:/disc/users/fulanito:/bin/csh
user3:axX/MxQZr37tA:0:3:James Iha:/disc/users/menganito:/bin/csh
Unix Change Password Command
where the password will be something like '*' or 'x' or anything whichcontains an asterisc '*' as '*NOPASSWORD*'. In this case, the file/etc/passwd is of no use, as Shadow Passwords or NIS is installed. Then, you may try doing a 'ypcat /etc/passwd' With this you may probablyfind via screen the real list of passwords. In the event you donthave enough rights to run 'ypcat', or if it isnt installed or if afterdoing it junk appears again, you will have to make use of other programsto obtain the passwords. I reccommend you PWGET. It is veryeasy to find, just look for PWGET.TAR.GZ or PWGET.TGZ in any archie, orin Lycos or in Yahoo. Sure you will find it. Once youhave it, you just need to upload it to the server you want to hack, unzipit ('gzip -d -f PWGET.TGZ'), untar it ('tar -x -f PWGET.TAR'), compileit ('cc -o pwget pwget.c') and run it ('./pwget') by which you will seein the screen the password list. If you want the list in a file,you just have to redirect the screen output into a file:$ ./pwget > fileThe same way you will redirect the output under DOS.. Now, for downloadingthe file you may use FTP, Kermit or the ZModem/Ymodem/Xmodem. Fordownloading the file via kermit or Zmodem you will need that your telnetprogram supports this protocols (as NetTerm), and that the Unix machinealso does (that is, it has the neccesary file installed). Kermitis usually installed in all systems:$ kermit
or else
$ ypcat /etc/passwd > file
or else
$ cat /etc/passwd > file
kermit> set file type ascii (or '
Default Unix Password
text', depends onsystems)kermit> set send pack 1000
kermit> set rec pack 1000
kermit> set file type 2 (or 3, as you prefer)
kermit> send fichero
.. Download->Kermit
CTRL+C
kermit> quit
$
.. Download->ZModem
$
Step 3: Cracking the password list
Now that you have the password list and several word lists, you need aprogram which encrypts the words and afterwards checks them with the encryptedpasswords in the password list. There are many programs you may use. Now I will briefly comment the characteristics of the programs (an theirnames, so that you may look for them in the net), but first I would liketo give some tips for obtaining the passwords in less time.CRACKERS:Delete from the password file all lines whose password is invalid ('*','*NOPASSWORD*', etc) Arrange the lines of the password file by the two first characters of theencrypted password. Some of the programs I comment, do this automatically,but some dont. With these two steps you may save a lot of time dependingin the cracker you use. Those users who have the password field empty
(user1::101:1:Manolito:/usr/user1:/bin/sh) dont have a passwordat all, therefore they are lines you may delete from the file. Whenyou login, simply by typing the username you will have access. Andin the event it asks you for a password, press ENTER without writing apassword. :-)
Here you have a table comparing all the different crackers. In the same machine and with the same word and password lists. Someof them took too long, and I aborted the proccess of cracking the passwords. In this cases, I calculated the estimated time they will take to finishaccording to the time taken (1 hour) and the amount of words checked forthat time.Cracker Jack 1.4 (JACK14*.*, CJACK*.*) It is the most extended in use,unleast as far as I know. It is almost in every hacking site of internet. Works under DOS and OS/2, and is quite fast. In the same 'distribution'there are many utilities which treat the word list. You may searchfor it in the web. Brute 2.00 (BRUTE*.*) Another cracker quite popular even beeing so slow. I think there is a faster version, but uses an encrypting algorythm whichisnt completely correct (although it is faster), and therefore it doesntcrack all passwords it should. I havent found any copy of this version,which means i wasnt able to test it. Works under DOS. StarCrack 0.64ß (STARCRAK*.*) This is a cracker with plenty of options,which allows to handle words while they are tested. It is quickerthan Cracker Jack, works under DOS and is very complete. It is quitenew, and is also a Beta, so i expect a much better version comming soon..:-? Has plenty of options and allows doing all kinds of things. You can find it at the StarCrack homepage: http://www.chez.com/thes/starcrak.html Hades 1.00a (HADES*.*) Another cracker for DOS. This works differentfrom the rest of crackers. Instead of encrypting a word and checkingit against the passwords of all users, it encrypts all the words and thenchecks them with the password of a user. Once it has finished withone user, it follows on with the next one. Due to this way of working,it makes too much I/O of disk, which slows down the whole proccess. It's output is slightly improved if we arrange the password file by theencrypted password field, as this way the cracker will check various usersat the same time. It can also be improved by having all the lists(password and word lists) in memory in a virtual disc. Guess 2.1 (GUESS*.*) Cracker for DOS, extremelly slow. It has memoryproblems if we try to use it with password files with more than 1000 lines PCUPC 2.01 (PCUPC*.*) Another cracker for DOS. This one has memoryproblems if we try to crack password files with more than 600/700 lines. Killer Cracker 9.5 (DJKC95*.*, KC*.*) As Guess, a very slow cracker forDOS and which gives problems with password files longer than 1000 lines. Xit 2.0 (XIT20*.*) Cracker for DOS. It is the slowest i've found.As its name says, it is a SHIT! :-) HellFire Cracker 1.3 (HC130*.*) Cracker for Dos. Requires a 386 with co-processorso it can work, but for some strange reason it hangs in my pentium andin my 486, therefore i cant tell you how good it is. Maybe if youhave a 386 you'll be able to use it satisfactory. The program includesa 387 emulator, just in case you dont have a co-processor. Any way,it is a very old program which surely wont be very fast. John the ripper 1.4 (UCFJOHN3*.*) Cracker for DOS/Win32/Linux and any othersystem, as it is distributed together with the source code. Worksin a similiar way to Cracker Jack but includes more options and is quitefast. It is a new release (when the doc was written :) courtesy ofUCF (United Cracking Force) and may be a bit difficult to find, but itis really useful and fast. It doesnt have as many options as theStar Crack, but is much faster. It even allows many options for treatingthe word list you use.. This is the homepage of John the Ripper: http://www.false.com/security/john/
These are the results, ordered by speed:
Unix Password Policy
| Cracker | Time | Checks per second | Comments |
|---|---|---|---|
| John the ripper 1.4 | 6'15' | 26667c/s | . |
| John the ripper 1.31 | 6'30' | 25641c/s | . |
| John the ripper 1.0 | 8'05' | 20619c/s | . |
| Star Crack 0.64ß | 9'15' | 18018c/s | . |
| Star Crack 0.51ß | 11'25' | 14599c/s | . |
| Cracker Jack 1.4 | 13'33' | 12300c/s | . |
| Cracker Jack 1.3 386 | 14'55' | 11173c/s | . |
| Cracker Jack 1.3 8086 | 22'22' | 7452c/s | . |
| Hades 1.00a | 47'05' | 3540c/s | . |
| Brute 2.00 | (est)59'54' | 2782c/s | . |
| PCUPC 2.01 | (est)135'37' | 1229c/s | Only allows passwordfiles shorter than 500 lines |
| Guess 2.1 | (est)141'58' | 1174c/s | Only allows passwordfiles shorter than 1000 lines |
| Killer Cracker 9.5 | (est)151'12' | 1105c/s | Only allows passwordfiles shorter than 1000 lines |
| Xit 2.0 | (est)195'37' | 852c/s | . |
| Hellfire Cracker 1.3 | infinito | 0c/s | It hanged and couldn'tbe tested |
This test was carried on a Pentium 133, with 16mb RAM, with all thedata in the hard disc, with a reading cache of 2mb and without pre-processingthe password file or the the word list. The word list contained 10000 words and the password file 1 000 passwords. 554 passwords hadto be found. Some of them took too long so i estimated the time accordingto what they have cracked until the moment of stopping them, thereforei dont know if they would have found all the passwords. I havejust included them in the table, in case some of you uses it. Youcan now see there are better things!
Tekken 3 Game Free Download for pc full version windows 7 setup with a single and direct download link. It is an action and fighting game with new characters different skills and powers Tekken 3 Overview Tekken 3.
As you can see, John the Ripper encrypts almost two times more passwords per seconds than the Cracker Jack. Guitar pro 5.1 download. I must admittthat the file with which i made the testing seems to be quite favorableto John the Ripper, as 20 000 c/s cant be obtained very often. Anyway,the comparison is significative of the speed by which the passwords arecracked by each of the programs.
I hope that with this mini-introduction to the art of crackingUnix passwords you can enjoy a good time; and I also hope that I haven'tbored you too much. If you have any question/comment/suggestion/destructive-comment,you may send an e-mail to z3b4l@iname.com.Greetings! ;-)
And for any comment about the traslation, you may also send mail to:toksuri@thepentagon.com(dont be too hard with your comments :c)
(C) 1997-2001 by !Hispahack
Para ver el web en las mejores condiciones, usa una resoluciónde 800x600 y Netscape Navigator
